IoBit Protected Folder life time registered key:: 75%: Easy File And Folder Protector 4.1. Folder Marker Pro 4.2 serial folder marker pro 4.3.0.0 serial. Folder Marker Pro Serial, Folder Marker Crack and Free Download of Full version 4.3 with Key, Torrent Download. Are you looking for Folder Marker Serial key, crack or full download?
Bloody v7 ultra core 3 keygen. (one of my odlest tutorials, sorry for bad quallity:/ ) FINNALY NEW CRACK IS HERE CHECK MY NEW VIDEO: THIS WILL NOT WORK IF U INSTALLED BLOODY 5 FIRST, SORRY. READ or die xD!
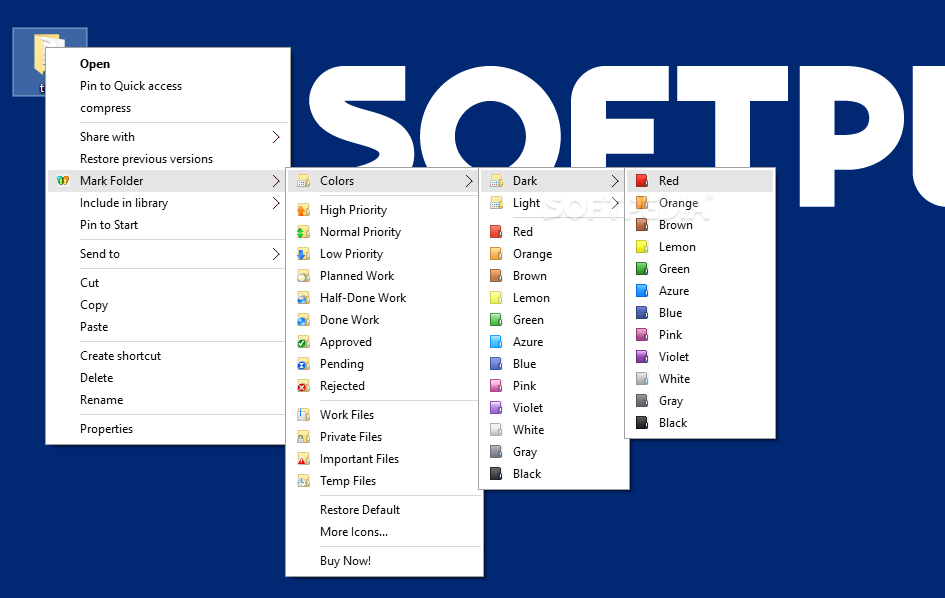
Folder Marker Pro Crack
Top 4 Download periodically updates software information of Folder Marker Pro - Changes Folder Icons 4.2 full version from the publisher, but some information may be slightly out-of-date.
Using warez version, crack, warez passwords, patches, serial numbers, registration codes, key generator, pirate key, keymaker or keygen for Folder Marker Pro - Changes Folder Icons 4.2 license key is illegal and prevent future development of Folder Marker Pro - Changes Folder Icons 4.2. Download links are directly from our mirrors or publisher's website, Folder Marker Pro - Changes Folder Icons 4.2 torrent files or shared files from free file sharing and free upload services, including Folder Marker Pro - Changes Folder Icons 4.2 Rapidshare, MegaUpload, HellShare, HotFile, FileServe, YouSendIt, SendSpace, DepositFiles, Letitbit, MailBigFile, DropSend, MediaMax, LeapFile, zUpload, MyOtherDrive, DivShare or MediaFire, are not allowed!
Folder Marker Pro 4.2 Download
Your computer will be at risk getting infected with spyware, adware, viruses, worms, trojan horses, dialers, etc while you are searching and browsing these illegal sites which distribute a so called keygen, key generator, pirate key, serial number, warez full version or crack for Folder Marker Pro - Changes Folder Icons 4.2. These infections might corrupt your computer installation or breach your privacy. Folder Marker Pro - Changes Folder Icons 4.2 keygen or key generator might contain a trojan horse opening a backdoor on your computer. Hackers can use this backdoor to take control of your computer, copy data from your computer or to use your computer to distribute viruses and spam to other people.
Most Popular Articles
- Download Midi Dangdut Untuk Orgen Tunggal
- Btp-2100e Driver Win7
- Powerpoint Animation Free Download 2012
- Cara Merubah Apk Ke Tpk
- Anime Hajime No Ippo Rising Sub Indo
- Terceiro Travesseiro Pdf
- Aggiornamento Software United Dvbt 9082
- Video One Piece All Episode Sub Indonesia Mp4
- Bullet 3d Girl Evolution Mod
- Rumi To Jawi Text Converter
- Fm 2005 Tactics
- Cara Menggunakan Subtitle Workshop Software
- Audition Redbana Perfect Hack Gamerzplanet
- Download Lagu Hadad Alwi Kaulah Ibuku Cinta Kasihku
- Cisco Asa Keygen
- Mitsubishi Asa Program Download
- Para Que Sirve Synaptics Pointing Device Driver Windows 7
- Easy Worship 2009 Tagalog Bible
- Lks Matematika Sd Kelas 3
- Bohren And Der Club Of Gore Sunset Mission Rar
- Tamil Actress Sex Image Gif
- Latest Stroke Scribe Keygen 2017 - Download Software 2017
- Comprehensive Meta Analysis Keygen
- Anime Saint Seiya Omega Sub Indo Full Episode
- 3d Max 64 Bit Download Crack Minecraft
- Magic Iso Maker Portable Download
- Amex Optima/oasis Program
- Hemisync The Gateway Experience Torrent
- Pokemon Liquid Crystal Walkthrough Pdf
- Poison Greatest Hits Album Torrent
- Download Lagu Rohani Katolik Bahasa Latin
- Xenoblade Chronicles Wii Iso Pal Torrent
- Download Bank Soal Ips Smp Kelas 8